Unveiling the Secrets: The Real Stories Behind Hackers, Intruders, and Deceivers

: Step into the Shadowy World of Cybersecurity
Welcome to the enigmatic world of cybersecurity, where the lines between hero and villain often blur. In this article, we embark on a thrilling journey into the real-life exploits of hackers, intruders, and deceivers who have left an indelible mark on the digital landscape. Prepare to encounter cybercriminals whose cunning escapades have caused chaos and compromised sensitive data, as well as cybersecurity professionals whose relentless efforts have safeguarded our interconnected world.
4.7 out of 5
| Language | : | English |
| File size | : | 1196 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 458 pages |
| Lending | : | Enabled |
Chapter 1: The Notorious Hackers – Masterminds of Cyberspace
1.1 Kevin Mitnick: The World's Most Elusive Hacker

Kevin Mitnick, a name synonymous with hacking prowess, captivated the world with his audacious exploits. His ability to manipulate social interactions and infiltrate secure systems earned him the reputation as the world's most elusive hacker. Mitnick's story serves as a chilling reminder of the devastating consequences that can arise from unchecked cybercrime.
1.2 Anonymous: The Decentralized Force of Cyber Activism

Anonymous, a decentralized collective of activists, has emerged as a formidable force in the realm of cyber activism. Their coordinated attacks and disruptive tactics have targeted governments, corporations, and individuals, challenging conventional power structures and raising awareness about pressing social issues.
Chapter 2: The Intruders – Breaching Boundaries and Exploiting Vulnerabilities
2.1 The Stuxnet Worm: A Cyber Weapon of Mass Destruction
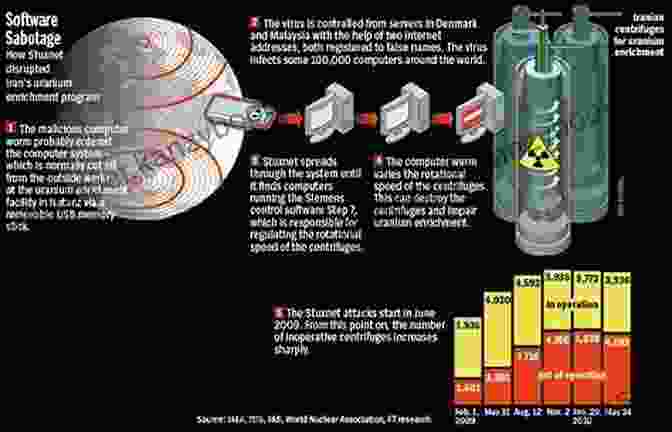
The Stuxnet worm stands as a chilling example of how cyber weapons can wreak havoc in the real world. Developed by a consortium of nation-states, Stuxnet targeted Iran's nuclear facilities, causing significant damage and disrupting their uranium enrichment program. This incident highlighted the alarming potential of cyber warfare and its far-reaching implications.
2.2 The Heartbleed Bug: A Critical Vulnerability with Devastating Consequences

The Heartbleed bug, discovered in 2014, exposed a gaping security flaw in the OpenSSL encryption library used by countless websites and servers. This critical vulnerability allowed attackers to steal sensitive data, including passwords, credit card numbers, and personal information, from vulnerable systems.
Chapter 3: The Deceivers – Masters of Manipulation and Fraud
3.1 The Nigerian Prince Scam: A Classic Example of Online Fraud
The Nigerian Prince scam, a long-running online fraud, continues to deceive unsuspecting victims with promises of vast wealth and inheritance. Preying on human greed and gullibility, this scam has resulted in millions of dollars in losses worldwide.
3.2 The Social Media Influencer Fraud: A Modern Twist on Deception

In the age of social media, a new breed of deceivers has emerged: social media influencers who engage in fraudulent practices. From purchasing fake followers to promoting deceptive products, these individuals exploit the trust of their followers for personal gain.
Chapter 4: The Cybersecurity Defenders – Guardians of the Digital Realm
4.1 The Cybersecurity Professionals: Defending Against Cyber Threats

Behind the scenes, a dedicated army of cybersecurity professionals works tirelessly to safeguard our digital world. These experts possess a deep understanding of cyber threats and employ cutting-edge technologies to protect organizations and individuals from malicious attacks. Their efforts are crucial in maintaining the integrity and security of our interconnected systems.
4.2 The White Hat Hackers: Ethical Defenders of Cyberspace

White hat hackers, also known as ethical hackers, are the unsung heroes of cybersecurity. They employ their hacking skills for good, identifying and fixing security vulnerabilities before malicious actors can exploit them. Their contributions are essential in strengthening our defenses against cyber threats.
: Lessons from the Shadows of Cybersecurity
As we conclude our journey into the realm of hackers, intruders, and deceivers, it is imperative to reflect on the lessons we have learned. These stories serve as cautionary tales, highlighting the devastating consequences of unchecked cybercrime and the importance of robust cybersecurity measures. However, they also showcase the heroic efforts of cybersecurity professionals and ethical hackers who work tirelessly to protect us from harm.
In this ever-evolving digital landscape, it is our collective responsibility to stay informed about cyber threats and take proactive steps to protect ourselves and our organizations. By educating ourselves, raising awareness, and supporting the work of cybersecurity professionals, we can create a more secure and resilient digital world for all.
4.7 out of 5
| Language | : | English |
| File size | : | 1196 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 458 pages |
| Lending | : | Enabled |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Molly Stevens
Molly Stevens Mary Ann Hoberman
Mary Ann Hoberman Kam Thye Chow
Kam Thye Chow Katherine Mason
Katherine Mason Sara Givens
Sara Givens Kathy Sierra
Kathy Sierra Melissa Cady D O
Melissa Cady D O Myah Master
Myah Master K L Montgomery
K L Montgomery Keith Provance
Keith Provance Kathleen Valentine
Kathleen Valentine Ma Rivera
Ma Rivera Kelly Peloza
Kelly Peloza Karyn Shanks Md
Karyn Shanks Md Sarah Kate Benjamin
Sarah Kate Benjamin Kate Tietje
Kate Tietje Kate Rosetti
Kate Rosetti Kevin Revolinski
Kevin Revolinski Zel Allen
Zel Allen Katie Wolf
Katie Wolf
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!
 Junot DíazFollow ·2.1k
Junot DíazFollow ·2.1k Forrest ReedFollow ·10.7k
Forrest ReedFollow ·10.7k Jeremy MitchellFollow ·17.1k
Jeremy MitchellFollow ·17.1k Galen PowellFollow ·11.3k
Galen PowellFollow ·11.3k Shannon SimmonsFollow ·15.7k
Shannon SimmonsFollow ·15.7k Xavier BellFollow ·12.3k
Xavier BellFollow ·12.3k Joseph FosterFollow ·5.1k
Joseph FosterFollow ·5.1k Anton FosterFollow ·19.1k
Anton FosterFollow ·19.1k

 Ethan Mitchell
Ethan MitchellDzogchen Nonmeditation: A Revolutionary Teaching Series...
Dzogchen Nonmeditation Dzogchen Teaching...

 Samuel Taylor Coleridge
Samuel Taylor ColeridgeThe Scariest One Of All Disney Short Story Ebook
Are you a fan of...

 Joe Simmons
Joe SimmonsThe Dzogchen Busuku Dzogchen Teaching Series: A Path to...
In the vast...

 Raymond Parker
Raymond ParkerUnlock the Secrets of Flawless English: A Comprehensive...
Are You Plagued by Penmanship Perils? Are you...

 Denzel Hayes
Denzel HayesUnderstanding Performance Through Physics, Physiology,...
Prologue: The Tripartite Foundation of Human...
4.7 out of 5
| Language | : | English |
| File size | : | 1196 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 458 pages |
| Lending | : | Enabled |